Deliverable D-Detailed Design
ECT 455 E-Commerce Web Engineering
Autumn 2011
Deliverable D: Detail Design Document
Team Yellow:
Mykle Brossette, Brian
Green, Satyam Kaneria & Jessica LoPresti
Link to Assignment:
ectweb2.cs.depaul.edu/yellow46/deliverables/deliverableD.html
PROJECT DEFINTION AND SCOPE:
Pet Match will
be a web and mobile solution for animal shelters and rescues that matches
adoptable pets with interested adopters based on their personality preferences.
Use of the site and mobile app will be free for both shelters and their
customers in order to attract consumer interest and to support shelters’
efforts to engage and screen adoption candidates.
The scope of
site functionality includes: Users will be able to create accounts, search database of
available pets, view a detailed profile for each pet, take a pet personality
quiz to receive customized matches, “like” and hide pets from list of recommended matches, manage
preferences on the user profile page, inquire for more information about individual pets and
submit adoption applications online.
OVERVIEW OF APPLICATION CHANGES:
Technical
Requirements
The site will be built using PHP as a server
side language, XHTML and HTML as front end with Javascript
and CSS for design purposes. Access will be used to create the database.
The following modules may be in place:
1.)
Authentication for end users and shelter
admins
2.)
Module that ranks and recommends pets based on
personality characteristics of pets and users
3.)
A registration module to allow members to save
their contact info and trait preferences
4.)
A simple administrative module with CRUD
functionality for site employees to manage pet profiles
5.)
Module to allow users to submit online adoption
applications
6.)
Ability for users to filter matching results
based on pet species (i.e. cat, dog, ferret, etc...)
Functional
Requirements:
1) User
create account
2) User
sign in (username and password)
3)
Adoption application
4)
Database of available pets
5)
Search for pets
6)
Personality preferences quiz/form
7) Recommended
matches
There are no changes to requirements to the
system:
1) Create User Account
#3 --A registration module to
allow members to save their contact info and trait preferences
2) Sign-in to site
# 1 --Authentication for end
users and shelter admins
3) Fill out pet match personality
#2 --Module that ranks and
recommends pets based on personality characteristics of pets and users
4) Search for a Siamese Cat in 60660
# 6 ---Ability for users to
filter matching results based on pet species (i.e. cat, dog, ferret, etc...)
5) From recommended matches choose a pet to adopt
and fill out form
#5 --
Module to allow users to submit online adoption applications
SIGNIFICANT ALGORITHMS:
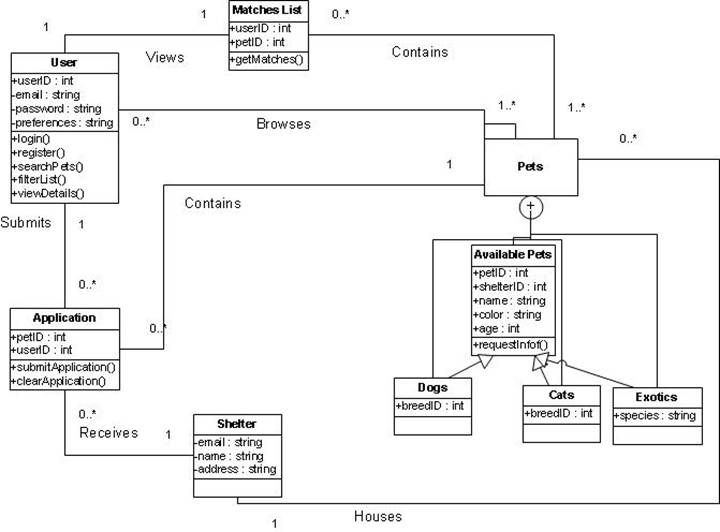
Description of classes:
User – this class will contain
user information for authentication/registration and will be used for
displaying personalized data on the profile page.
Application
– this class will reference the authenticated user’s information as well as the
selected pet’s and will be used to submit the user’s information related to
their interest in adopting the referenced pet. This class will generate an
email that will be sent to the shelter housing the pet.
Shelter
– this class is a data entity containing information about shelters and will be
used to populate the shelter information in the pet profile as well as route
submitted applications.
Matches List
– this class will be used to generate an updated list of the pets most closely
matching the authenticated user’s preferences.
Pets – this package contains the
Available Pets class as well as the subclasses for dogs, cats and exotics. This
is a data entity that populates the matches list as well as search results when
users browse available pets.
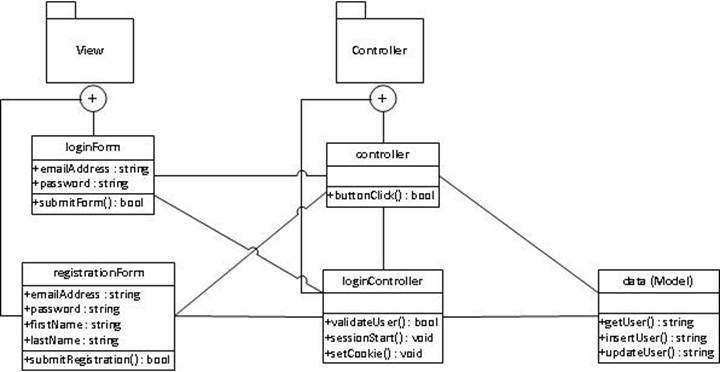
How will we implement the MVC or design
patterns?
We will separate the presentation layer (view),
the business logic layer (controller) and the data layer (model). The data
layer will be responsible for establishing connections with the database. The
connections will be stored in a separate file and “included” in the data layer.
The data layer will also store the connective commands in order to perform
queries and database CRUD commands. The business layer will supply the
validation and other rules. For an example of the MVC structure, we’ll take
user login functionality. First, the user interacts with the login form, which
is the presentation layer or view. When the user submits the login form, the
business logic layer (controller) responds with an event receiver that triggers
operators that validate the user input and trigger a database query from the
model, supplying the user’s input values as variables. The data layer (model)
queries the database using the supplied variables, returning a bool value to the controller. Based on that result, the
controller may return a false statement to the presentation layer, or else will
create a new session, set the session ID and store a cookie, and will then
return “true” to the presentation layer, which will then pass the user to the
profile. In this way, each class interacts with the others and performs
specific duties within the login process.
This class diagram illustrates the MVC design
pattern for the user login and registration processes:
DATA STRUCTURES:
ERD MODEL:
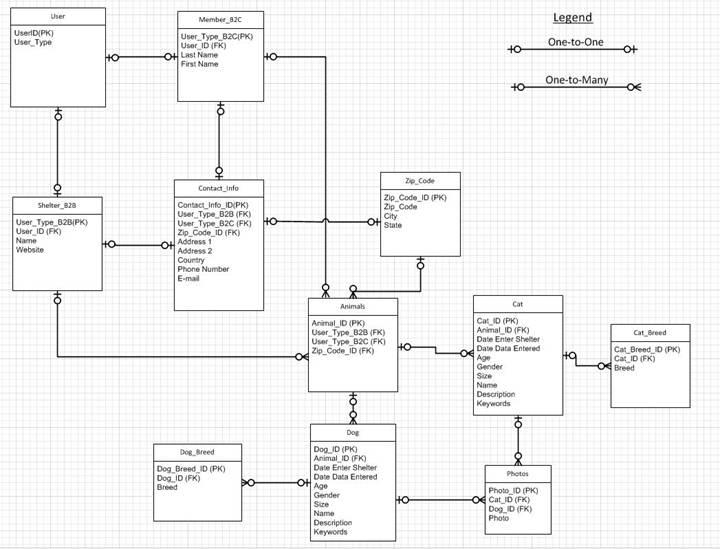
Data Structures (Data Models and Tables)
User
UserID(PK) - Unique
User_Type – Not Null
Member_B2C
User_Type_B2C(PK) -
Unique
User_ID (FK) – Not Null
Last Name
First Name
Shelter_B2B
User_Type_B2B(PK) -
Unique
User_ID (FK) – Not Null
Name – Not Null
Website
Contact Information
Contact_Info_ID(PK) - Unique
User_Type_B2B (FK) –
Not Null
User_Type_B2C (FK) –
Not Null
Zip_Code_ID (FK) – Not Null
Address 1
Address 2
Country
Phone Number (If
e-mail is null than phone # can’t be null)
E-mail (If phone
number is null than e-mail can’t be null)
Zip Code
Zip_Code_ID (PK) - Unique
Zip_Code – Not Null
City – Not Null
State – Not Null
Animals
Animal_ID (PK) - Unique
User_Type_B2B (FK) –
Not Null
User_Type_B2C (FK) –
Not Null
Zip_Code_ID (FK) – Not Null
Cat
Cat_ID (PK) - Unique
Animal_ID (FK) – Not Null
Date Enter Shelter –
Not Null
Date Data Entered –
Not Null
Age
Gender – Not Null
Size
Weight
Name – Not Null
Description
Keywords – Not Null
Dog
Dog_ID (PK) - Unique
Animal_ID (FK) – Not Null
Date Enter Shelter –
Not Null
Date Data Entered –
Not Null
Age
Gender – Not Null
Size
Weight
Name – Not Null
Description
Keywords – Not Null
Dog Breed
Dog_Breed_ID (PK) - Unique
Dog_ID (FK) – Not Null
Breed – Not Null
Cat Breed
Cat_Breed_ID (PK) - Unique
Cat_ID (FK) – Not Null
Breed – Not Null
Photos
Photo_ID (PK) - Unique
Cat_ID (FK) – Not Null
Dog_ID (FK) – Not Null
Photo
Data Definition
Languages
DROP TABLE USER
CASCADE CONSTRAINTS;
DROP TABLE MEMBER_B2C
CASCADE CONSTRAINTS;
DROP TABLE SHELTER_B2B
CASCADE CONSTRAINTS;
DROP TABLE
CONTACT_INFO CASCADE CONSTRAINTS;
DROP TABLE ZIP_CODE
CASCADE CONSTRAINTS;
DROP TABLE ANIMALS
CASCADE CONSTRAINTS;
DROP TABLE CAT CASCADE
CONSTRAINTS;
DROP TABLE DOG CASCADE
CONSTRAINTS;
DROP TABLE DOG_BREED
CASCADE CONSTRAINTS;
DROP TABLE CAT_BREED
CASCADE CONSTRAINTS;
DROP TABLE PHOTOS
CASCADE CONSTRAINTS;
CREATE
TABLE USER(
UserID CHAR (5) NOT NULL PRIMARY KEY,
User_Type CHAR (3) NOT NULL
);
CREATE
TABLE Member_B2C(
User_Type_B2C
CHAR (5) NOT NULL PRIMARY KEY,
UserID CHAR (5) NOT NULL FOREIGN KEY,
Last
Name CHAR (15) NOT NULL,
First
Name CHAR (15) NOT NULL
);
CREATE
TABLE Shelter_B2B(
User_Type_B2B
CHAR (5) NOT NULL PRIMARY KEY,
UserID CHAR (5) NOT NULL FOREIGN KEY,
Name
CHAR (30) NOT NULL,
Website
CHAR (45)
);
CREATE
TABLE Contact_Info(
Contact_Info_ID CHAR (5) NOT
NULL PRIMARY KEY,
User_Type_B2C
CHAR (5) NOT NULL FOREIGN KEY,
User_Type_B2B
CHAR (5) NOT NULL FOREIGN KEY,
Zip_Code_ID CHAR (10)
NOT NULL FOREIGN KEY,
Address
1 CHAR (30),
Address
2 CHAR (15),
Country
CHAR (15),
Phone
Number CHAR (13,
E-mail
CHAR (30)
);
CREATE
TABLE Zip_Code(
Zip_Code_ID CHAR (10)
NOT NULL PRIMARY KEY,
City
CHAR (15) NOT NULL,
State
CHAR (15) NOT NULL
);
CREATE
TABLE Animals(
Animal_ID CHAR (10) NOT NULL PRIMARY KEY,
User_Type_B2C
CHAR (5) NOT NULL FOREIGN KEY,
User_Type_B2B
CHAR (5) NOT NULL FOREIGN KEY,
Zip_Code_ID CHAR (10)
NOT NULL FOREIGN KEY,
);
CREATE
TABLE Cat(
Cat_ID CHAR (5) NOT NULL PRIMARY KEY,
Animal_ID CHAR (10) NOT NULL FOREIGN KEY,
Date
Entered Shelter CHAR (15) NOT NULL,
Date
Data Entered CHAR (15) NOT NULL,
Age
CHAR (2),
Gender
CHAR (6),
Size
CHAR (6),
Weight
INT (2),
Name
CHAR (30),
Description
CHAR (240)
Keywords
CHAR (120)
);
CREATE
TABLE Dog(
Dog_ID CHAR (5) NOT NULL PRIMARY KEY,
Animal_ID CHAR (10) NOT NULL FOREIGN KEY,
Date
Entered Shelter CHAR (15) NOT NULL,
Date
Data Entered CHAR (15) NOT NULL,
Age
CHAR (2),
Gender
CHAR (6),
Size
CHAR (6),
Weight
INT (2),
Name
CHAR (30),
Description
CHAR (240)
Keywords
CHAR (120)
);
CREATE
TABLE Cat_Breed(
Cat_Breed_ID CHAR (5) NOT
NULL PRIMARY KEY,
Cat_ID CHAR (10) NOT NULL FOREIGN KEY,
Breed
CHAR (15) NOT NULL,
);
CREATE
TABLE Dog_Breed(
Dog_Breed_ID CHAR (5) NOT
NULL PRIMARY KEY,
Dog_ID CHAR (10) NOT NULL FOREIGN KEY,
Breed
CHAR (15) NOT NULL,
);
CREATE
TABLE Photos(
Photo_ID CHAR (5) NOT NULL PRIMARY KEY,
Dog_ID CHAR (5) NOT NULL FOREIGN KEY,
Cat_ID CHAR (5) NOT NULL FOREIGN KEY,
Photo
BLOB
);
INSERT INTO USER
VALUES (‘1234’,’B2B’);
INSERT INTO MEMBER_B2C
VALUES (‘12345’, ‘1234’, ‘Christensen’, ‘Mary’);
INSERT INTO SHELTER_B2B
VALUES (‘12345’, ‘1234’, ‘Animal Savior’,
‘animalsavior.org’);
INSERT INTO CONTACT_INFO
VALUES (‘23456’, ‘12345’, ‘12345’, 60660, ‘123
Alphabet St.’, ‘Apt. 23’, ‘USA’, 345-345-2345, ‘mChristensen@gmail.com’);
INSERT INTO ZIP_CODE
VALUES (60660, ‘Chicago’, ‘Illinois’);
INSERT INTO ANIMALS
VALUES (‘23456’, ‘12345’, ‘12345’, 60660);
INSERT INTO CAT
VALUES (‘56789’, ‘23456’,
TO_DATE('1/23/2009','MM/DD/YYYY'), TO_DATE('1/23/2009','MM/DD/YYYY'), ‘2’,
‘Female’, ‘12’, ’small’, ‘Rogue’, ‘Friendly furry creature that doesn’t like
other cats or dogs. Best to family with no other pets. Very playful.’ ,
‘Playful, Loving, Low Attention’);
INSERT INTO DOG
VALUES (‘56789’, ‘23456’,
TO_DATE('1/23/2010','MM/DD/YYYY'), TO_DATE('1/23/2010','MM/DD/YYYY'), ‘5’,
‘Male’,’35’, ’medium’, ‘Charlie’, ‘Friendly
and Playful. He was in an abusive home and needs lots of love.’,
’Friendly, Lazy, Playful’);
INSERT INTO CAT_BREED
VALUES (‘12345’, ‘2345’, ‘Burmese’);
INSERT INTO DOG_BREED
VALUES (‘12345’, ‘2345’, ‘Beagle’);
INSERT INTO PHOTOS
VALUES (‘65789’, ‘12345’, ‘23456’, “Charlie.jpg”);
ALTER TABLE MEMBER_B2C
ADD CONSTRAINT
B2C_USER_ID_FK FOREIGN KEY (User_ID) REFERENCES
USER (User_ID);
ALTER TABLE MEMBER_B2B
ADD CONSTRAINT
B2B_USER_ID_FK FOREIGN KEY (User_ID) REFERENCES
USER (User_ID);
ALTER TABLE
CONTACT_INFO
ADD CONSTRAINT
CONTACT_USER_TYPE_B2B_ID_FK FOREIGN KEY (User_Type_B2B_ID) REFERENCES
SHELTER_B2B
(User_Type_B2B_ID);
ALTER TABLE
CONTACT_INFO
ADD CONSTRAINT
CONTACT_USER_TYPE_B2C_ID_FK FOREIGN KEY (User_Type_B2C _ID) REFERENCES
MEMBER_B2C
(User_Type_B2C _ID);
ALTER TABLE
CONTACT_INFO
ADD CONSTRAINT
CONTACT_ZIP_CODE_ID_FK FOREIGN KEY (Zip_Code_ID)
REFERENCES
ZIP_CODE (Zip_Code_ID);
ALTER TABLE ANIMALS
ADD CONSTRAINT
ANIMALS_USER_TYPE_B2B _ID_FK FOREIGN KEY (User_Type_B2B _ID) REFERENCES
SHELTER_B2B
(User_Type_B2B _ID);
ALTER TABLE ANIMALS
ADD CONSTRAINT
ANIMALS_USER_TYPE_B2BC_ID_FK FOREIGN KEY (User_Type_B2C_ID) REFERENCES
MEMBER_B2C
(User_Type_B2C_ID);
ALTER TABLE ANIMALS
ADD CONSTRAINT
ANIMALS_ZIP_CODE_ID_FK FOREIGN KEY (Zip_Code_ID)
REFERENCES
ZIP_CODE (Zip_Code_ID);
ALTER TABLE CAT
ADD CONSTRAINT
CAT_ANIMAL_ID_FK FOREIGN KEY (Animal_ID) REFERENCES
ANIMAL (Animal_ID);
ALTER TABLE DOG
ADD CONSTRAINT
DOG_ANIMAL_ID_FK FOREIGN KEY (Animal_ID) REFERENCES
ANIMAL (Animal_ID);
ALTER TABLE CAT_BREED
ADD CONSTRAINT
BREED_CAT_ID_FK FOREIGN KEY (Cat_ID) REFERENCES
CAT (Cat_ID);
ALTER TABLE DOG_BREED
ADD CONSTRAINT
BREED_DOG_ID_FK FOREIGN KEY (Dog_ID) REFERENCES
DOG (Dog_ID);
ALTER TABLE PHOTOS
ADD CONSTRAINT
PHOTOS_DOG_ID_FK FOREIGN KEY (Dog_ID) REFERENCES
DOG (DOG_ID);
ALTER TABLE PHOTOS
ADD CONSTRAINT
PHOTOS_CAT_ID_FK FOREIGN KEY (Cat_ID) REFERENCES
CAT (Cat_ID);
SQL
STATEMENTS
SELECT
* FROM CAT
WHERE Gender='Male'
AND
WHERE
Age
BETWEEN
1 AND 5
____________________________________
SELECT
Breed FROM DOG_BREED
WHERE
Breed = ‘Dachsund’
UNION ALL
SELECT * FROM DOG
WHERE
DOG_BREED.Dog_Breed_ID = DOG.Dog_Breed_ID
_______________________________________________
SELECT
* FROM ANIMALS
WHERE
User_Type_B2C = ‘person logged in ID’
UNION
ALL
SELECT
* FROM DOG, CAT
WHERE
DOG.Animal_ID = ANIMALS.Animal_ID
AND
CAT.Animal_ID = ANIMALS.Animal_ID
__________________________________________________
SELECT Name, Website FROM SHELTER_B2B
SELECT
* FROM CAT
WHERE
Gender = ‘Female’
AND
WHERE
Age
BETWEEN
1 and 5
AND
Where
Keywords LIKE ‘ % Friendly % Lazy’
INTERFACE DESIGN:
Website Wireframes:
Pet Match Home Page:
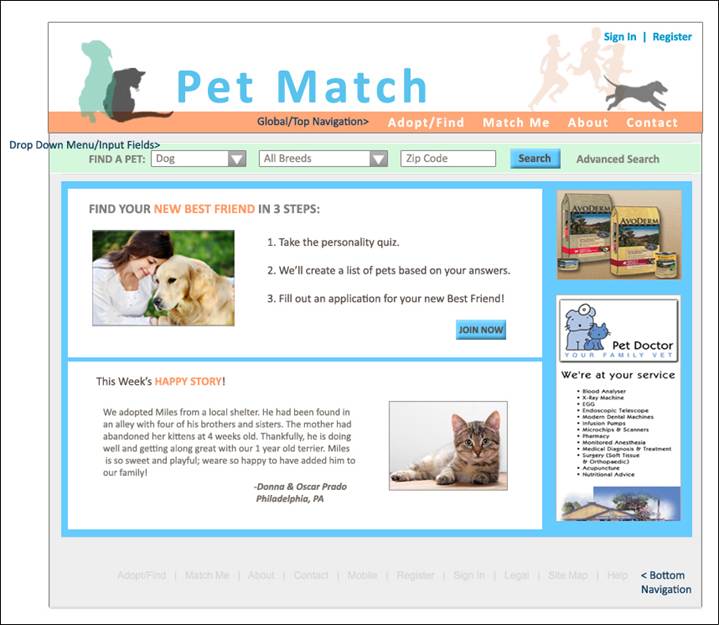
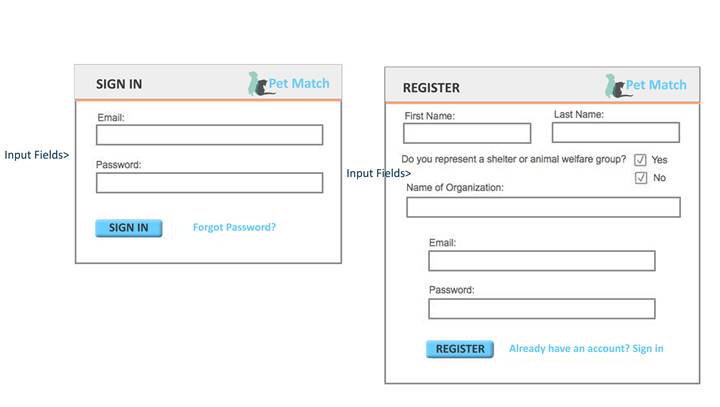
Sign In/Register Forms:
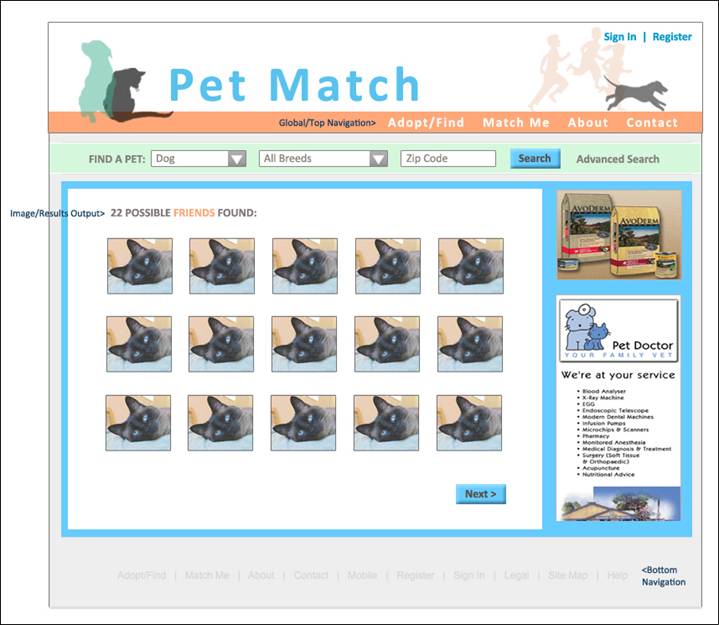
Adopt/Find a Pet Page:

Search Results Page:
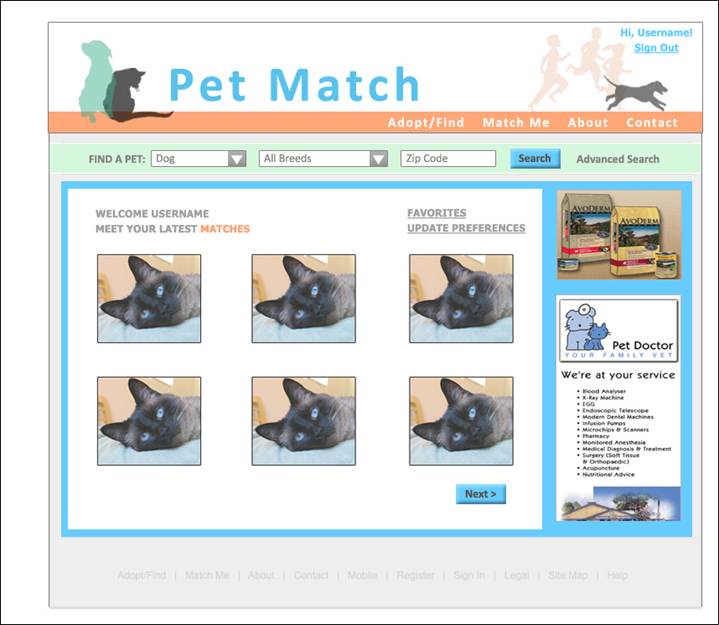
User Profile Page:
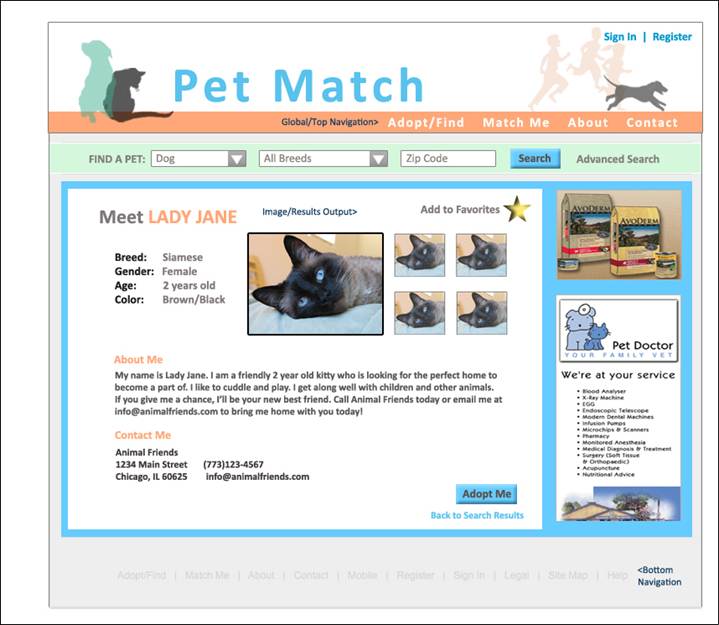
Pet Profile Page:
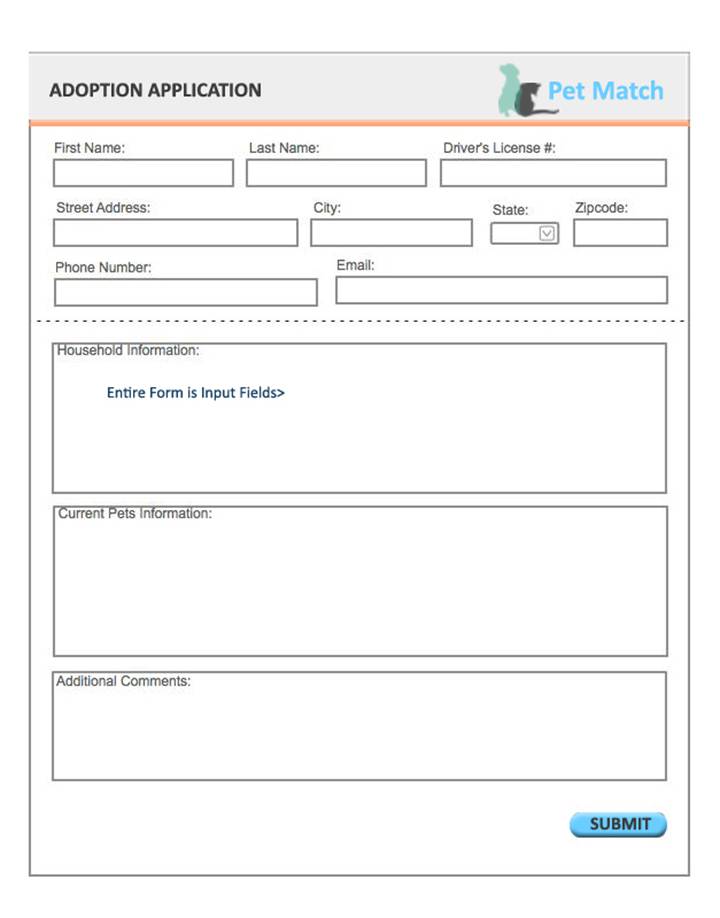
Adoption Form:
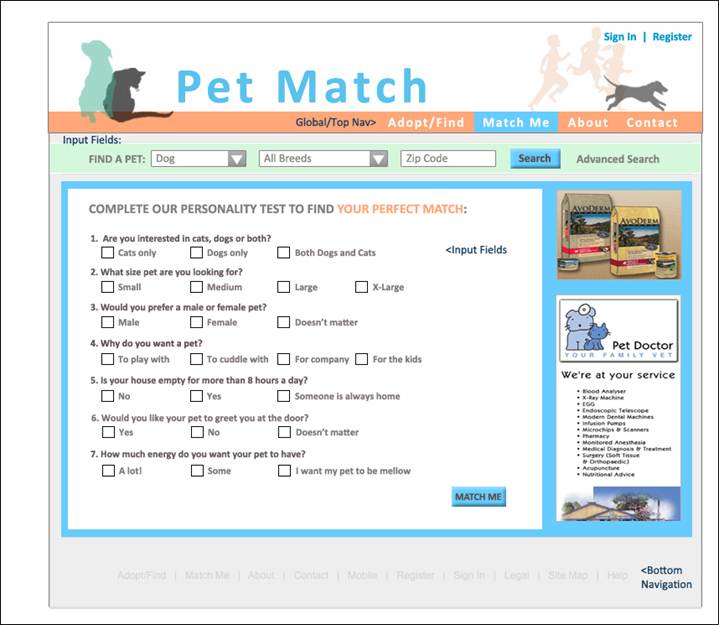
Personality Quiz Page:
Mobile Wireframes:
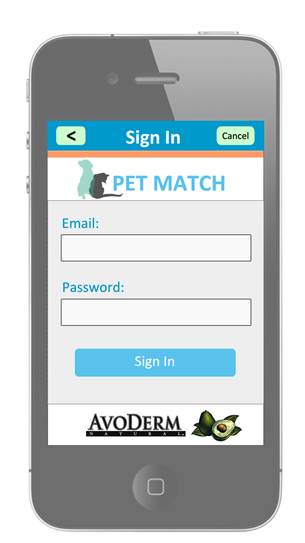
Sign In Screen:
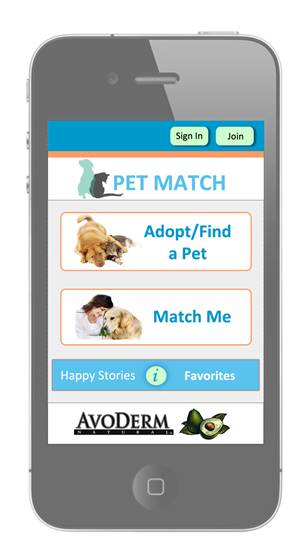
Main Screen:
Adopt/Find a Pet Screen:
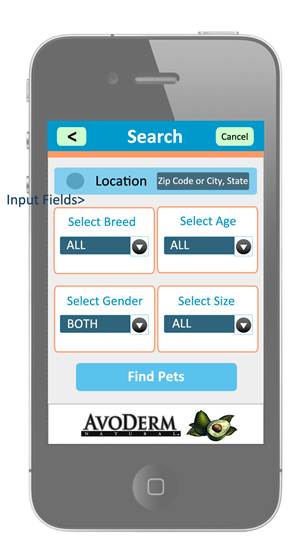
Search Results Screen:
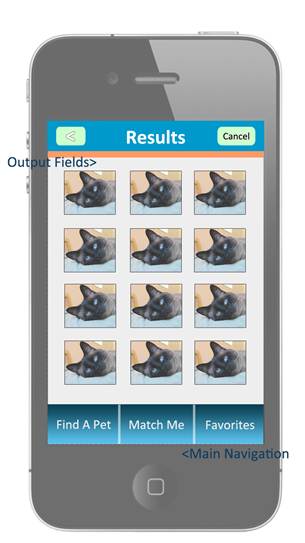
Pet Profile Screen:
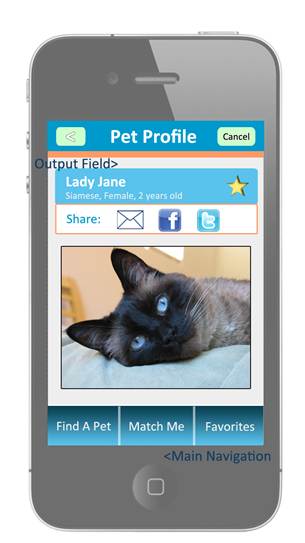
SECURITY REQUIREMENTS:
Pet Match is an organization that aims to
provide its business service in a way that is secure enough for the customers
to feel safe with sharing or storing information on the site. Pet Match will
try to store minimum information needed to conduct business, however, enough
security measures will be taken to meet the industry standards. Although there
are range of security measures available based on the budget and type of
organization, below are the options that Pet Match finds suitable for its
purpose.
Following security measures will be taken for
all the forms used on the site.
1) At the client level, all the web forms will
implement JavaScript that will check for input length and usable characters or
numbers.
2) On the server end, PHP script will used to
verify the input length of form field allowed and if the characters were part
of the allowed set or not.
3) Both JavaScript (client end) and PHP (server
end) will use Regular Expression for email check. (/^[a-zA-Z0-9._-]+@[a-zA-Z0-9.-]+\.[a-zA-Z]{2,4}$/)
Below are the steps that will be taken to
secure the server.
1) The server will implement public-key
cryptography based 128-bit SSL certificate from Verisign
Certificate Authority. It is one of most commonly used methods to secure
websites and it provides vulnerability assessment and daily website malware
scanning. In addition, Verisign is one of the leading
Certificate Authorities and is well supported by most modern browsers.
For login and authentication purpose, the users
will be asked to choose a password that is 6 characters or more in length, uses
one number, one capital alphabet character and one symbolic character.
Other security measures will include the
recording the login time and date and IP address for records.
USABILITY TESTING:
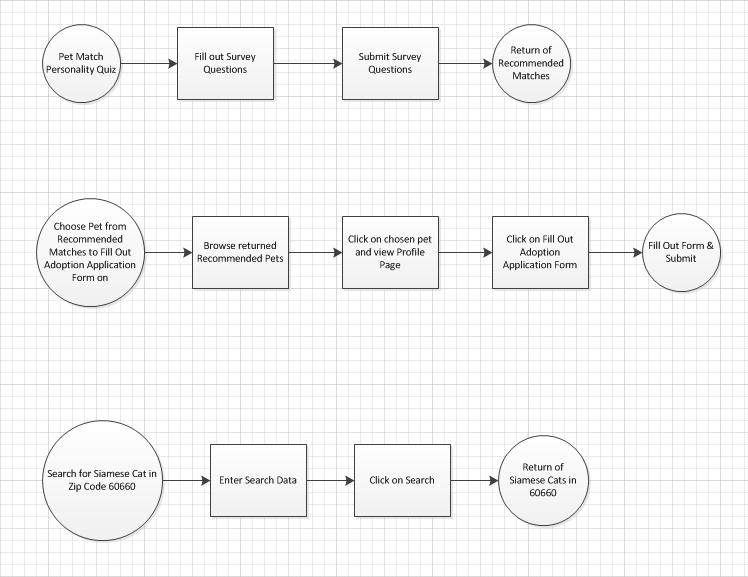
Usability Testing Task List
Five Requirements for Site:
For
both Website and Mobile:
1)
Create User Account
2)
Sign-in to site
3)
Fill out pet match personality
4)
Search for a Siamese Cat in 60660
5)
From recommended matches choose a pet to adopt and fill out form
Original Technical Requirements:
The
site will be built using PHP as a server side language, XHTML and HTML as front
end with Javascript and CSS for design purposes.
Access will be used to create the database.
The
following modules may be in place:
1. Authentication
for end users and shelter admins
2. Module that
ranks and recommends pets based on personality characteristics of pets and
users
3. A
registration module to allow members to save their contact info and trait
preferences
4. A simple
administrative module with CRUD functionality for site employees to manage pet
profiles
5. Module to
allow users to submit online adoption applications
6. Ability for
users to filter matching results based on pet species (i.e. cat, dog, ferret,
etc...)
Usability Testing Task List and Matching to Appropriate Design
Requirement:
1) Create User
Account
#3 A registration module to allow members to save their contact
info and trait preferences
2) Sign-in to
site
#1 Authentication for end users and shelter admins
3) Fill out pet
match personality
#2 --Module that ranks and
recommends pets based on personality characteristics of pets and users
4) Search for a
Siamese Cat in 60660
# 6 -- Ability for users to filter matching results based on pet
species (i.e. cat, dog, ferret, etc...)
5) From
recommended matches choose a pet to adopt and fill out form
#5 -- Module to allow users
to submit online adoption applications
Expected Response Time is based on GOMS-KLM and is timed for
expert users of the system. Any time over the expected time is relevant to
novice users of the system and will be calculated with the GOMS-KLM as the
baseline for testing.
Legend for
GOMS-KLM
P, Point the mouse to an object on screen --- 1.10 seconds
B, Button press or release (mouse) --- 0.10 seconds
H, Hand from keyboard to mouse or vice versa --- 0.40 seconds
M, Mental Preparation --- 1.20 seconds
K1 = average speed keystrokes (0.20 seconds)
K2 = typing random letters (0.50 seconds)
Web-Site
1) Create User Account
M, P, B, H, M, Time to fill in information - about 40 keystrokes avg 40+K1 and 8 keystroked random 8+K2, H, P, B
1.2 + 1.1 + .10 + .40 + 1.2 + 40*.2 + 8*.5 + .4 + 1.1 + .10 = 16.8
seconds
2) Sign-in to Site
M, P, B, H, type in info - about 20 keystrokes avg
20+K1 and 8 keystrokes random 8+K2, H, P, B
1.2 + 1.1 + .1 + .40 + 20*.2 + 8*.5 + .4 + 1.1 + .10 = 12.4
seconds
3) Fill out Pet Match
M, P, B, H, filling out form - about 7 questions P & B - 7+P
and 7+B with 7+M, H, P, B
1.2 + 1.1 + .1 + .40 + 7*1.2 + 7*.1 + 7*1.2 + .4 + 1.1 + .10 =
21.9 seconds
4) Search for Siamese Cat in 60660
M, P, B, P, B, P, B, H, H, P, B
1.2 + 1.1 + .10 + 1.1 + .10 + 1.1 + .10 + .4 + .4 + 1.1 + .10 =
6.8 seconds
5) From Recommended Matches Choose a Pet to Adopt and Fill out
Form
M, P, B, M, P, B, M, H, M, 120*k2, M, H, P, B
1.2 + 1.1 + .10 + 1.2 + 1.1 + .10 + 1.2 + .40 + 1.2 + 120*.5 + 1.2
+ .40 + 1.1 + .10 = 70.4 seconds
Mobile Site
1) Create User Account
M, B, M, B, M, B, B, M, B, B
1.2 + .10 + 1.2 + .10 + 1.2 + .10 + .10 + 1.2 + .10 + .10 = 5.4
seconds
2) Sign-in to Site
M, B, M, B
1.2 + .10 + 1.2 + .10 = 2.6 seconds
3) Fill out Pet Match
M, B, M, B, M, B, M, B, M, B
1.2 + .10 + 1.2 + .10 + 1.2 + .10 + 1.2 + .10 + 1.2 + .10 = 6.5
seconds
4) Search for Siamese Cat in 60660
M, B, M, B, M, B
1.2 + .10 + 1.2 + .10 + 1.2 + .10 = 3.9 seconds
5) From Recommended Matches Choose a Pet to Adopt and Fill out
Form
M, B, M, B, M, B, M, B, M, B
1.2 + .10 + 1.2 + .10 + 1.2 + .10 + 1.2 + .10 + 1.2 + .10 = 6.5
seconds
WEB/MOBILE SITE DELIVERABLE:
URL WEBSITE: http://ectweb.cs.depaul.edu/yellow46/index.php
MOBILE
SITE: http://ectweb.cs.depaul.edu/yellow46/mobile/index.php
MEMBER CONTRIBUTIONS:
Mykle Brossette:
·
Overview of Application
Changes
·
Data Structures
·
Usabilty Testing
Brian Green:
·
Significant Algorithms
·
Website template deliverable
Satyam Kaneria :
·
Security Requirements
·
Mobile site deliverable
Jessica LoPresti:
·
Interface Design for web and
mobile applications
·
Compiled/Edited portions of
the final deliverable
